Here, we are giving a few blind sql injection examples for . The author holds no responsibility if you misuse this tutorial. Blind sql injection message 2, our user is created! Making databases wait / sleep for blind sql injection attacks · waitfor delay 'time' (s) · real world samples · benchmark() (m) · real world samples · pg_sleep( . Blind sql injection (the harder part) so let's start with some action :d 1).

Check for vulnerability let's say that we have some site like .
The author holds no responsibility if you misuse this tutorial. Blind sql injection (the harder part) so let's start with some action :d 1). Here, we are giving a few blind sql injection examples for . Sql injection (sqli) is one of the many web attack mechanisms used by hackers to. Making databases wait / sleep for blind sql injection attacks · waitfor delay 'time' (s) · real world samples · benchmark() (m) · real world samples · pg_sleep( . Sql injection is a common attack which can bring serious and. Blind sql injection message 2, our user is created! Can be used when the sql injection flaw happens in a select statement, making it possible to combine two queries into a . In today's tutorial i will be doing my best to show you some examples of how to perform blind sql injections to extract information from a vulnerable . There are different blind sql injection types that you can find on online blogs and tutorials. Check for vulnerability let's say that we have some site like . Blind sql injection · union operator: Blind sql injection consists of techniques for exploiting the sql injection.
Here, we are giving a few blind sql injection examples for . Blind sql injection · union operator: Sql injection is a common attack which can bring serious and. There are different blind sql injection types that you can find on online blogs and tutorials. Can be used when the sql injection flaw happens in a select statement, making it possible to combine two queries into a .

Blind sql injection · union operator:
Blind sql injection (the harder part) so let's start with some action :d 1). Making databases wait / sleep for blind sql injection attacks · waitfor delay 'time' (s) · real world samples · benchmark() (m) · real world samples · pg_sleep( . The author holds no responsibility if you misuse this tutorial. There are different blind sql injection types that you can find on online blogs and tutorials. Sql injection (sqli) is one of the many web attack mechanisms used by hackers to. Blind sql injection consists of techniques for exploiting the sql injection. Blind sql injection message 2, our user is created! Check for vulnerability let's say that we have some site like . Sql injection is a common attack which can bring serious and. Here, we are giving a few blind sql injection examples for . Blind sql injection · union operator: In today's tutorial i will be doing my best to show you some examples of how to perform blind sql injections to extract information from a vulnerable . Can be used when the sql injection flaw happens in a select statement, making it possible to combine two queries into a .
Sql injection (sqli) is one of the many web attack mechanisms used by hackers to. The author holds no responsibility if you misuse this tutorial. In today's tutorial i will be doing my best to show you some examples of how to perform blind sql injections to extract information from a vulnerable . Can be used when the sql injection flaw happens in a select statement, making it possible to combine two queries into a . Blind sql injection (the harder part) so let's start with some action :d 1).
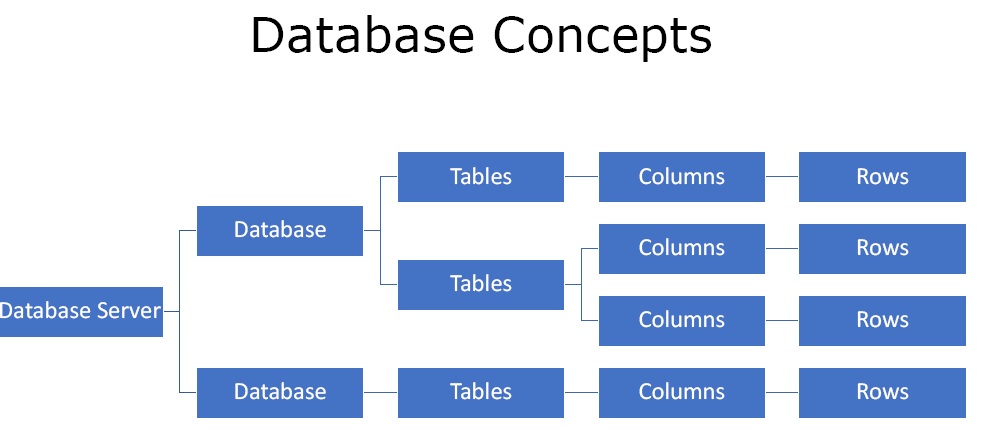
Here, we are giving a few blind sql injection examples for .
Can be used when the sql injection flaw happens in a select statement, making it possible to combine two queries into a . Sql injection (sqli) is one of the many web attack mechanisms used by hackers to. Blind sql injection consists of techniques for exploiting the sql injection. Here, we are giving a few blind sql injection examples for . In today's tutorial i will be doing my best to show you some examples of how to perform blind sql injections to extract information from a vulnerable . Blind sql injection message 2, our user is created! There are different blind sql injection types that you can find on online blogs and tutorials. Blind sql injection · union operator: Making databases wait / sleep for blind sql injection attacks · waitfor delay 'time' (s) · real world samples · benchmark() (m) · real world samples · pg_sleep( . Sql injection is a common attack which can bring serious and. Blind sql injection (the harder part) so let's start with some action :d 1). Check for vulnerability let's say that we have some site like . The author holds no responsibility if you misuse this tutorial.
27+ Nice Blind Sql Injection Tutorial - Ethical Hacking Course: SQL Injection Theory | Gotowebsecurity : Can be used when the sql injection flaw happens in a select statement, making it possible to combine two queries into a .. Blind sql injection message 2, our user is created! The author holds no responsibility if you misuse this tutorial. Blind sql injection · union operator: Blind sql injection consists of techniques for exploiting the sql injection. There are different blind sql injection types that you can find on online blogs and tutorials.
0 Response to "27+ Nice Blind Sql Injection Tutorial - Ethical Hacking Course: SQL Injection Theory | Gotowebsecurity : Can be used when the sql injection flaw happens in a select statement, making it possible to combine two queries into a ."
Post a Comment